Blog
Future Digital Transformation Trends Worth Knowing
Dec 09, 2022

This global digital transformation trend forces us to explore what will be the key future digital transformation trends in 2022 and upcoming years. So, let's explore some of the vital digital transformation trends we are most likely going to see in the near future. But first, let's quickly look at the significance of digital transformation today.
Read More5 Things to Consider Picking Public Cloud Service
Nov 18, 2022

There are many leading public cloud services available today, such as Amazon Web Services (AWS), Microsoft Azure, Google Cloud, IBM Cloud, etc. However, it is not an easy job to pick one service out of them because different businesses have different needs to fulfill. Therefore, this article will highlight 5 criteria to consider to select the right cloud service provider.
Read MoreWhy VPN is a Must for Businesses Today? - CARE IT
Oct 27, 2022
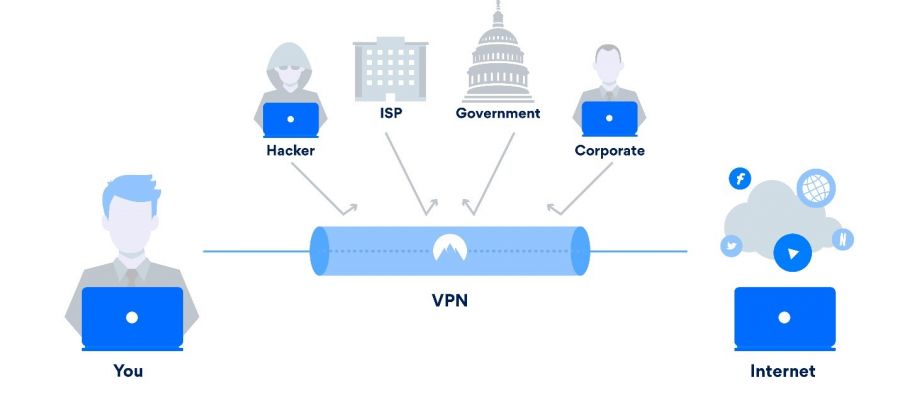
Virtual Private Networks (VPNs) were already in use at the individual level to bypass the geolocation restrictions, but they have now become popular in the business community. VPNs provide advanced security with easy to set up and use support.
Read MoreManaging SharePoint Storage Space on Microsoft365
Oct 11, 2022

SharePoint is one of the leading cloud-based content management platforms powered by Microsoft. SharePoint is assisting thousands of organizations in managing corporate content, creating websites, and storing and organizing data from any device.
Read MoreWhat are the Different Kinds of IT Engineers?
Sep 15, 2022

Since the digital infrastructure is becoming more complex and advanced, so does the roles around IT engineering. Today IT engineering is a very broad term, covering different kinds of IT engineers. Whether it's about system administration or security professionals, the IT engineer profession is diversifying at a rapid pace.
Read More6 Best Cybersecurity Practices for Remote Working
Aug 26, 2022

Remote working means employees will be using different devices from different locations to access the company's data resources. This means that companies cannot implement the same cybersecurity measures that they can implement on-premises.
Read MorePromising Step Towards Green IT
Aug 17, 2022

In simple words, it is a practice of using IT resources in an environmentally sustainable and efficient way. The main targets of green IT practices are to maximize the energy efficiency of computing devices, reduce the use of hazardous materials, and encourage the biodegradability of outdated products.
Read MoreCybersecurity Risk Assessment in 5 Steps
Jul 25, 2022

All organizations that use IT infrastructure and involve some form of internet connectivity are vulnerable to ever-growing cyber threats. It is essential for all such organizations to deploy intelligent and up-to-date cybersecurity measures.
Read More